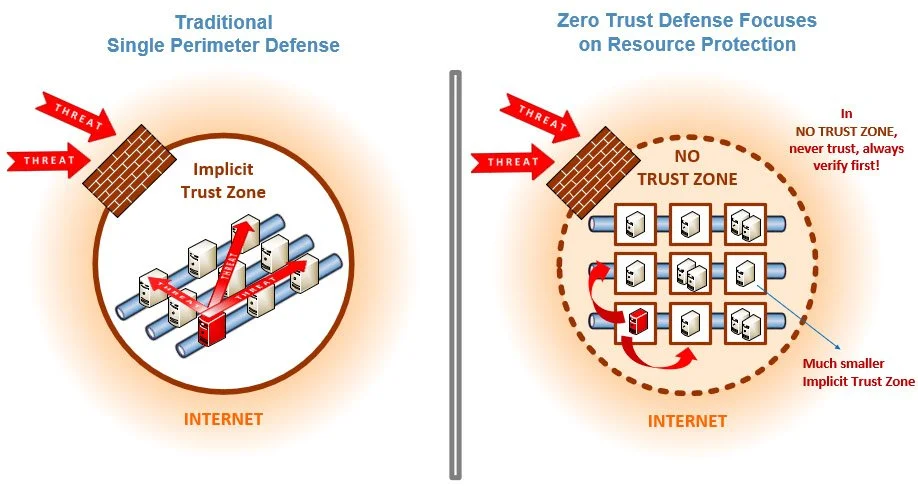
Is Your Business Prepared to Defend Against Cyberattacks and Data Breaches?
Deploy Zero Trust for a complete protection across your critical areas of risk: endpoints, workloads, data and identity
The Importance of Zero Trust in The Post-COVID World
According to IBM, the average cost of a data breach in 2022 was $4.24 million, and a ransomware attack averaged $1.85 million ⁽¹⁾. With the rise of remote workers, Zero Trust ensures that only authorised individuals and devices can access sensitive information, significantly reducing the risk of data breaches and cyber-attacks.
Here’s why everyone is looking at Zero Trust today:
Save at least $660,000 per breach even with a partially deployed Zero Trust solution.
Experience a 43% reduction in data breach costs with a fully deployed Zero Trust solution.
Organisations with high-standard encryption spend an average of $3.62 million per breach.
Detects and contains breaches 27% faster by leveraging AI and security automation alongside Zero Trust.
Source:
[1] https://www.ibm.com/reports/data-breach
Case Study:
Leading Solar Panel Manufacturer
Client Details:
At Techdirect, we have had the privilege of working with a global solar panel manufacturer that designs, manufactures and sells solar panels across 100+ countries. Renowned for their solar innovation, they possess access to 1000+ patents and offer best-in-class solar panel products known for record-setting efficiency and unmatched reliability.
Problem:
With their headquarters based in Singapore and operations spread worldwide, our client recognised the need for enhanced security measures in a post-Covid world. They aimed to protect their endpoints across different geographical locations, especially with the rise of remote work. Despite having some security measures in place, they desired a comprehensive approach to fortify their defences. Additionally, their IT team was relatively small, necessitating a solution that could offer robust protection without placing an excessive burden on their limited resources.
Process:
To address their challenges, we implemented the following Zero Trust solutions as part of their security enhancement strategy:
1) EDR - Endpoint Detection and Response
What is it: Endpoint Detection and Response (EDR) is a security technology designed to detect, investigate, and respond to security incidents on endpoints such as desktops, laptops, servers and mobile devices.
What we did: To secure their remote workforce using personal devices, we deployed Crowdstrike, a cloud-based endpoint protection solution. Powered by AI, Crowdstrike delivers real-time threat prediction and prevention, ensuring that their staff working from home are shielded from potential security risks.
2) CASB - Cloud Access Security Broker
What is it: Cloud Access Security Broker (CASB) is a security technology that provides organisations with visibility and control over the use of cloud services by employees and third-party vendors.
What we did: We implemented a Cloud Access Security Broker (CASB) to monitor and enforce security policies, preventing unauthorized access, data leakage, and risky behavior in the cloud. By analysing cloud traffic, CASB identified potential threats, applied data loss prevention measures, and ensured compliance with security and regulatory standards.
3) ZTNA - Zero Trust Network Access:
What is it: Zero Trust Network Access (ZTNA) is a security model that focuses on providing secure access to resources based on user or device identity and context, rather than relying solely on traditional network perimeters.
What we did: By adopting Zero Trust Network Access (ZTNA), we verified the trustworthiness of users and devices before granting access to sensitive resources. This reduced the risk of unauthorized access and lateral movement within the network, ensuring that only authenticated and authorized individuals or devices could access critical data.
4) VPN - Secure Remote Access
What is it: A Virtual Private Network (VPN) is a secure network connection that allows users to access a private network over the internet.
What we did: Through the implementation of Virtual Private Network (VPN) technology, we established a secure encrypted connection. This allowed remote employees to access network resources and applications while maintaining data confidentiality and integrity.
5) NDR - Network Detection and Response
What is it: Network Detection and Response (NDR) is a security technology that monitors and analyses network traffic to detect and respond to potential security threats.
What we did: For safeguarding their cloud infrastructure and data centres, we integrated Vectra, a comprehensive solution that covers traffic, network, applications, and data loss. Vectra enables continuous monitoring to detect and investigate attacks, ensuring the integrity and security of their cloud and data centre network.
6) MDR - Continuous Monitoring and Response
What is it: Managed Detection and Response (MDR) is a security service that combines advanced security technology with human expertise to provide continuous monitoring and response to potential security threats.
What we did: Our Managed Detection and Response (MDR) service combined advanced threat intelligence, security analytics, and expert analysts. This ensured real-time detection and investigation of security incidents, providing around-the-clock threat detection, rapid incident response, and ongoing security expertise.
Outcomes:
By implementing our Zero Trust solutions, our client achieved remarkable outcomes:
-

1. Strengthened Endpoint Security:
The adoption of Crowdstrike provided advanced protection to their remote workforce, safeguarding their critical data and ensuring a secure work environment, even when using personal devices.
-
2. Proactive Threat Detection:
With Vectra's robust network security capabilities, our client successfully detected and investigated potential attacks, preventing unauthorised access and minimising the risk of data breaches.
-

3. Global Security Management:
The implementation of the Zero Trust framework enabled centralised security management across their global operations, ensuring consistent and effective security measures regardless of geographical location.
-

4. Resource Optimization:
Despite having a small IT team, our client was able to maintain a high level of security across their infrastructure with the help of our integrated solutions, allowing them to focus their resources on other strategic initiatives.
While we cannot disclose the company's name due to security purposes, this case study highlights the successful implementation of our Zero Trust solutions for a solar panel manufacturer with a global presence.
Our Zero Trust Consultative Process
When you partner with us, we take the following steps to ensure your organisation's security:
-
Step 1: Identify Your Assets
First, we start by identifying and understanding the critical data and assets in your organisation that require protection. This includes sensitive data, essential applications, and other valuable resources unique to your business.
-

Step 2: Assess Your Risks
Our experts conduct a thorough risk assessment to uncover potential vulnerabilities and threats that may compromise your assets. By understanding your risk landscape, we can develop tailored security measures to mitigate these risks effectively.
-

Step 3: Develop a Security Strategy
Based on the findings from the risk assessment, we develop a comprehensive security strategy. This strategy includes the creation of robust policies and procedures for user and device authentication, access control, and ongoing monitoring.
-

Step 4: Implement Security Measures
We implement a range of security measures to safeguard your assets. These may include multi-factor authentication, network segmentation, encryption, intrusion detection systems, and firewalls. Our goal is to create layers of defence that fortify your infrastructure against both internal and external threats.
-

Step 5: Continuously Monitor and Analyze
Our team employs advanced monitoring and analysis tools to continuously monitor all network traffic. This proactive approach enables us to detect and respond swiftly to potential threats. With the help of analytics and artificial intelligence, we can identify anomalies and patterns indicative of malicious activity in real-time.
-
Step 6: Test and Refine
At Techdirect, we believe in the importance of regular testing and refinement of security measures. Our experts conduct periodic assessments, penetration tests, and security audits to ensure that your defences remain effective and up to date. By staying ahead of evolving threats, we help you adapt your security measures to address new vulnerabilities effectively.
Our Credentials
Certifications
Our team is equipped with industry-leading certifications and expertise to deliver exceptional IT services:
Cloudflare
Accredited Configuration Engineers
Accredited Solutions Architect
Red Hat
Certified Red Hat delivery Specialist (Automation)
Certified Red Hat System Administrator
Azure
Certified Ondemand Migration Specialist (Azure)
Jumpcloud
Accredited engineers who can deploy Jumpcloud
Project Management Professional (PMP)® Certification
Project Management Professional (PMP)® certification
Empowering Businesses Across ASEAN
Regional Offices
Our company has established a strong presence in the ASEAN region, with offices located in:
Singapore
Thailand
Philippines
Malaysia
Taiwan
Vietnam
Languages
We are proud to serve a diverse clientele, and our team is proficient in multiple languages, including: English, Thai, Tagalog, and Bahasa.
Protect Your Business Against Breaches With A Full Zero Trust Solution
Safeguard your organisation's sensitive data wherever it resides
Scale your IT security effortlessly as your business grows, ensuring protection for your expanding environment.
Embrace a comprehensive security framework that covers all aspects of your IT infrastructure, providing holistic protection against evolving threats.
Empower your small IT team by taking advantage of our 24/7 support as we provide the highest quality monitoring and incident response in the industry.